
Project Summary
Video Surveillance is becoming ubiquitous, except in those locations where privacy truly dominated. Unfortunately, surveillance may simply serve to displace crime. Richard Thomas, Acting Deputy Chief Constable for Gwent, U.K., told the BBC that he believed video surveillance simply pushed some crime beyond the range of the cameras [Flaherty-98]. This means that when designing vision-systems for security, broader questions need to be addressed. For example, a 1993 USA Weekend survey reported that 2,000 students were physically attacked each hour of the school day [Ansley-93]. The areas that are being watched (physically or by video) have reduced the incidents, but the areas that are not (because of cost) or cannot (because of privacy) have become havens. In the USA survey, nearly half of those surveyed said they avoided school restrooms out of fear [Ansley-93]. Video surveillance in the schools did not solve the problems; it just pushed them to a new location – one where cameras are not currently allowed. The significant market potential for this POCg is a technology that by developing privacy enhancing cameras we can enter submarkets of the 5B video surveillance market that have been heretofore untapped – from airport and school bathrooms to nursing homes, and provide a new alternative that enhances privacy and security in other settings. We believe it also has significant potential for the home security market.
The proposed project will take research that demonstrated, in an offline lab setting, privacy enhancements in video surveillance, and develop a fully operational real-time system where these ideas are embedded into the camera hardware and tested in the field. This camera will do in-place encryption of the parts of the image where there are people, thus protecting privacy. However, it will not encrypt motionless object and would remote viewers to see motionless people (after a delay), and can be decrypted in an emergency or with a key from a “warrant”. Thus it protects privacy but allows security operations that justified the need for surveillance in the first place.
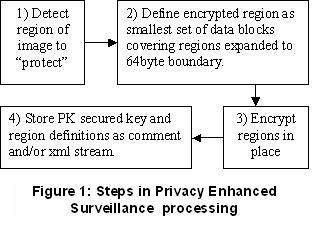
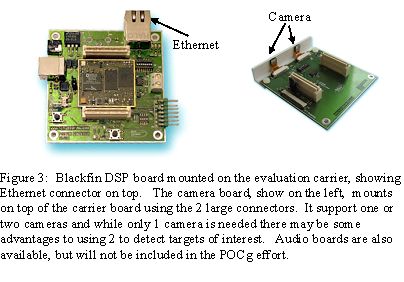
The key idea of the approach is to detect, through vision-based algorithms, areas of the scene that require “privacy” protection, and then use in-place public-key based encryption to protect that data. The steps are shown in figure 1, with an image showing the in place encryption after a motion-based detection of potential regions requiring privacy protection, with an example image shown in figure 2. The hardware is shown in figure 3.
 |
 |
|---|
 |
|---|
